Over the years, I've built and maintained multiple online cryptography tools - AES encryption, ChaCha20 encryption, RSA encryption, and several hashing utilities. On the surface, all these tools look simple: you provide some input, click a button, and get an encrypted or hashed output.
But while working on these tools and reading user questions and comments, I noticed a recurring pattern - many users are confused about why different algorithms require different inputs. Why does ChaCha20 need a nonce? Why does AES talk about modes and padding? Aren't they all just "encryption" at the end of the day?
This article exists to answer those questions in a practical, beginner-friendly way, while still being accurate for experienced developers.
Encryption Looks Simple - Until You Look Under the Hood
From a high level, most encryption tools appear identical. You enter plain text, provide a secret key, and receive encrypted output. This is true whether you are using AES, ChaCha20, or even older algorithms.
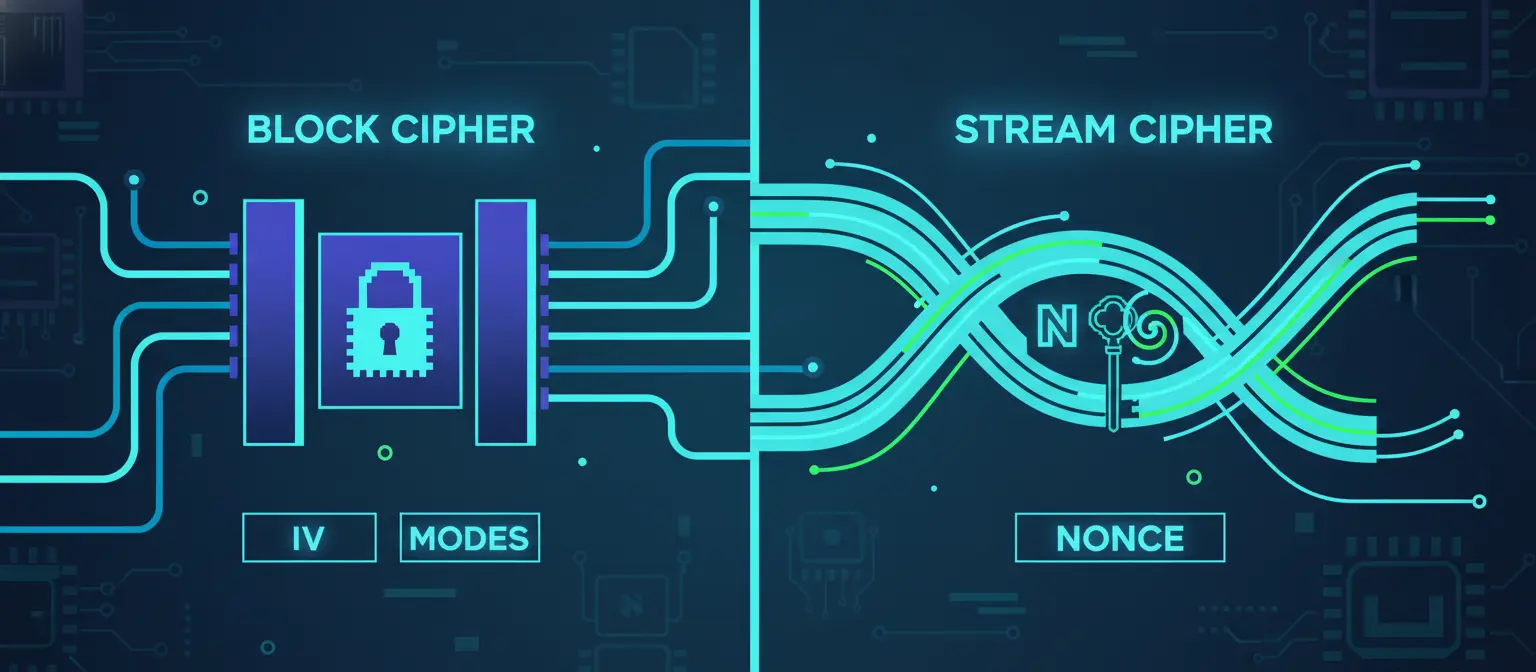
However, once you start implementing these tools, the differences become impossible to ignore. Some algorithms ask for an initialization vector (IV), some require a nonce, some expose modes, and others deliberately hide complexity to prevent misuse.
These differences are not accidental - they are a direct result of how each algorithm is designed.
What Is AES and Why Does It Have So Many Options?
AES (Advanced Encryption Standard) is a block cipher. This means it encrypts data in fixed-size blocks (128 bits at a time), rather than treating data as a continuous stream.
Because of this design, AES must be used with a mode of operation such as CBC, CTR, or GCM. Each mode defines how blocks are chained together and how randomness is introduced.
This is why AES tools often expose fields like:
- Encryption mode (CBC, GCM, etc.)
- Initialization Vector (IV)
- Padding scheme
These options give AES a lot of flexibility and power, but they also make it easier for inexperienced users to configure it incorrectly. AES is especially fast on modern CPUs because many processors include hardware acceleration (AES-NI), making it a popular choice for servers and desktops.
What Is ChaCha20 and Why Does It Need a Nonce?
ChaCha20 is fundamentally different. It is a stream cipher, meaning it generates a pseudorandom keystream and XORs it with the plaintext to produce ciphertext.
Instead of modes and padding, ChaCha20 relies on a few core inputs:
- A 256-bit secret key
- A nonce (number used once)
- An internal counter
Users often ask why ChaCha20 requires a nonce while AES sometimes does not expose one. The answer is simple: stream ciphers must never reuse the same keystream.The nonce ensures that even if the same key is reused, the encrypted output will always be different.
AES vs ChaCha20: Practical Comparison
| Aspect | AES | ChaCha20 |
|---|---|---|
| Encryption Type | Block cipher | Stream cipher |
| Standardization | NIST standard | IETF (RFC 8439) |
| Primary Random Input | IV (depends on mode) | Nonce |
| Key Size | 128 / 192 / 256 bits | 256 bits |
| Modes Required | Yes (CBC, GCM, etc.) | No |
| Padding | Often required | Not required |
| Hardware Acceleration | Yes (AES-NI) | No |
| Mobile Performance | Good | Excellent |
Why Many Users Find ChaCha20 Easier to Use Correctly
One thing I've noticed while maintaining encryption tools is that ChaCha20 leads to fewer configuration mistakes. There is no concept of "wrong mode" or "bad padding."
As long as users provide a unique nonce and a strong key, ChaCha20 behaves predictably and securely. This is one of the reasons it is widely used in modern TLS implementations, especially on mobile devices.
You can experiment with nonce and key behavior using a ChaCha20 encryption tool.
If you're unsure whether your encryption choices are safe, the Crypto Safety Validator tool can help highlight potential security issues before deployment.
When AES Still Makes More Sense
Despite the simplicity of ChaCha20, AES remains the default choice in many enterprise and server-side environments.
- Disk and database encryption
- High-throughput server applications
- Compliance-driven systems
- Platforms with AES hardware acceleration
In these cases, AES can be extremely fast and secure when used correctly. You can explore how different AES modes behave using an AES encryption tool.
When Should You Use ChaCha20?
ChaCha20 shines in environments where predictable performance and implementation safety matter.
- Mobile applications (Android, iOS)
- Embedded and IoT devices
- Browsers and JavaScript-based cryptography
- Systems without AES hardware acceleration
ChaCha20 is commonly paired with Poly1305 for authentication and is widely used in modern TLS configurations. You can test ChaCha20 behavior using an online ChaCha20 tool.
When NOT to Use AES
AES itself is secure, but incorrect usage can introduce vulnerabilities.
- Do not use AES in ECB mode for sensitive data
- Avoid custom or home-grown AES modes
- Do not reuse IVs in modes like CBC or CTR
Many real-world AES issues come from configuration mistakes rather than weaknesses in the algorithm itself.
When NOT to Use ChaCha20
- When legacy systems require strict AES-only compliance
- If hardware-accelerated AES is significantly faster in your environment
- When cryptographic libraries do not properly support ChaCha20-Poly1305
While ChaCha20 is robust, compatibility requirements may still favor AES in some enterprise systems.
Common Mistakes I See with Both Algorithms
- Reusing IVs or nonces
- Using AES-ECB because it "looks simpler"
- Confusing encryption with hashing
- Assuming all encrypted output is interchangeable
Most real-world cryptography failures happen not because the algorithm is broken, but because it was misunderstood.
Security and Performance Trade-offs
From a cryptographic standpoint, both AES and ChaCha20 are considered secure when implemented correctly. The real differences come down to performance characteristics and ease of correct usage.
AES benefits from decades of analysis and hardware support, while ChaCha20 offers simpler, safer implementations with consistent performance across platforms.
So, Which One Is Better?
There is no universally "better" algorithm.
- Choose AES for servers, storage encryption, and compliance-heavy systems.
- Choose ChaCha20 for mobile apps, browsers, and performance-constrained environments.
In many modern systems, both algorithms coexist, each optimized for different scenarios.
Frequently Asked Questions
Is ChaCha20 more secure than AES?
No. Both are considered secure. ChaCha20 is often easier to implement safely, while AES benefits from extensive hardware support and long-term analysis.
Why does TLS use ChaCha20?
TLS uses ChaCha20 primarily to improve performance on devices without AES hardware acceleration, such as mobile phones and low-power systems.
Can AES and ChaCha20 be used together?
Yes. Many systems support both and dynamically select the best option based on the client environment.
Conclusion
AES and ChaCha20 both solve the same high-level problem - turning readable data into unreadable data - but they approach it in very different ways.
If you understand why certain fields exist in your encryption tool, choosing the right algorithm becomes much easier. And in many modern systems, the best answer is not "AES or ChaCha20," but knowing when to use each.